Comparative Evaluation of Alpha-based Representative Binary Technique Toward Other Dual-bit Techniques Feature-based Method in Text Steganography
Keywords:
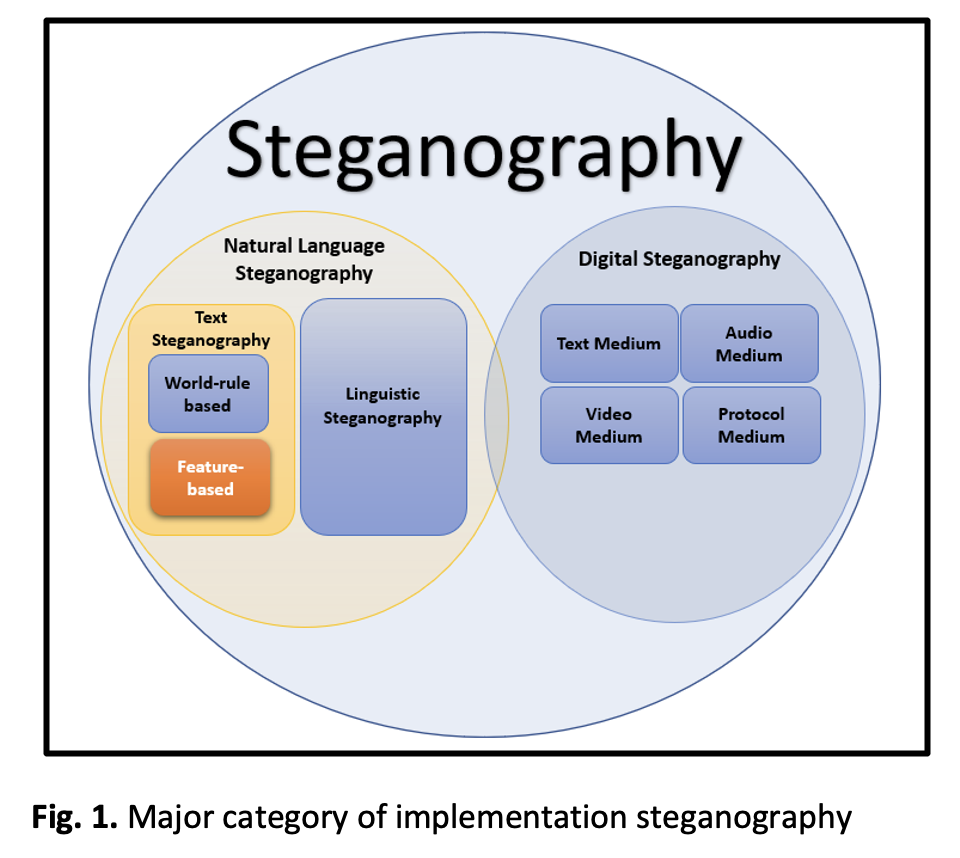
Feature-based Method, information hiding, Alpha-based Representative Binary, One-Flow-2-bit, Bit-One-Count, evaluation metricAbstract
This paper investigates the performance of three distinct feature-based text steganography techniques designed for secure data concealment. It evaluates the novel Alpha-based Representative Binary technique of feature-based method, which uses letter case (capital and small) to represent binary data, alongside the One-Flow-2-bit technique, which classifies letters by their visual writability, and the Bit-One-Count technique, which uses the count of '1' bits in a letter’s binary form. Using a standardized validation framework applied to a substantial dataset, the techniques are assessed on their core operational capabilities for embedding and extracting hidden messages. Key performance metrics, including precision, recall, accuracy, and F-measure, are employed to provide a quantitative and multi-faceted comparison. The findings offer critical insights into the relative strengths, limitations, and practical implications of each method, contributing to the evidence-based advancement of reliable text steganography for security applications. This paper provide also provides a clear, evidence-based framework for selecting effective text steganography methods in security applications